OPNsense Setup
\\ Information - OPNsense
OPNsense is a free and open-source firewall and routing platform based on FreeBSD. It is designed to provide network security and services like VPN and DNS, with a web-based graphical interface for easy configuration and management.
OPNsense offers a wide range of features and capabilities, such as:
- Firewall: Stateful packet filtering with support for NAT, port forwarding, and traffic shaping to block unwanted traffic and protect your network.
- VPN: OPNsense supports various VPN protocols, such as OpenVPN and IPsec, for secure remote access to the network.
- Intrusion Detection and Prevention System (IDPS): OPNsense includes Suricata, an open-source IDPS that can detect and prevent network intrusions.
- Web Filtering: OPNsense offers web filtering capabilities that can block access to specific websites and content categories. It also includes Sensei/ZenArmor: Optional add-ons that extend web filtering and security features with cloud-based threat intelligence and traffic analytics.
- DNS and DHCP: OPNsense can act as a DNS and DHCP server, providing these network services to devices on the network.
- High Availability: OPNsense supports high availability configurations, allowing for redundancy and failover in case of hardware or network failures.
- ZenArmor: ZenArmor is an add-on to OPNsense that provides advanced threat intelligence and security analytics capabilities. It uses machine learning algorithms to detect and prevent cyber attacks in real time.
OPNsense is typically used by organizations of all sizes to protect their networks and ensure secure access to their resources. It is popular among IT professionals and network administrators for its flexibility, ease of use, and community support. With the addition of Sensei and ZenArmor, OPNsense provides even more advanced security capabilities to protect against modern cyber threats.
Before making any changes to software, systems, or devices, it’s important to thoroughly read and understand the configuration options, and verify that the proposed changes align with your requirements. This can help avoid unintended consequences and ensure the software, system, or device operates as intended.
⚠️ A default OPNsense installation is functional but not hardened.
This guide helps you establish a secure baseline configuration before applying customizations.
\\ System > *
// Access
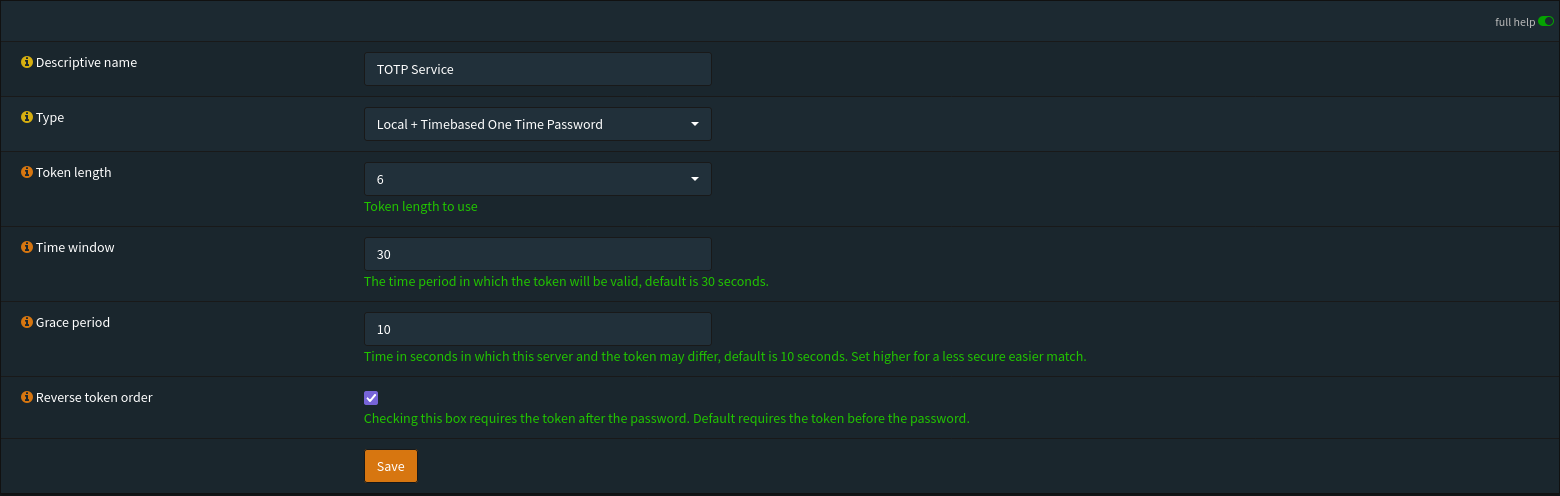
Always create individual admin accounts and protect them with TOTP.
- Go to System > Access > Servers and create a new service for TOTP.
- For each user, generate a seed under OTP seed and pair it with an authenticator app.
// Firmware > Plugins
Recommended plugins for a secure and manageable OPNsense setup.
- ZenArmor (formerly Sensei):
- os-sensei
- os-sensei-updater
- os-sunnyvalley
- os-ddclient - Dynamic DNS support.
- os-acme-client - Recommended for valid TLS certificates.
- os-net-snmp - For SNMP monitoring.
- os-qemu-guest-agent - For Proxmox/VM integration.
- os-theme-vicuna - Dark mode theme.
!!! Highly recommended to install for dark mode, bugs love light !!!
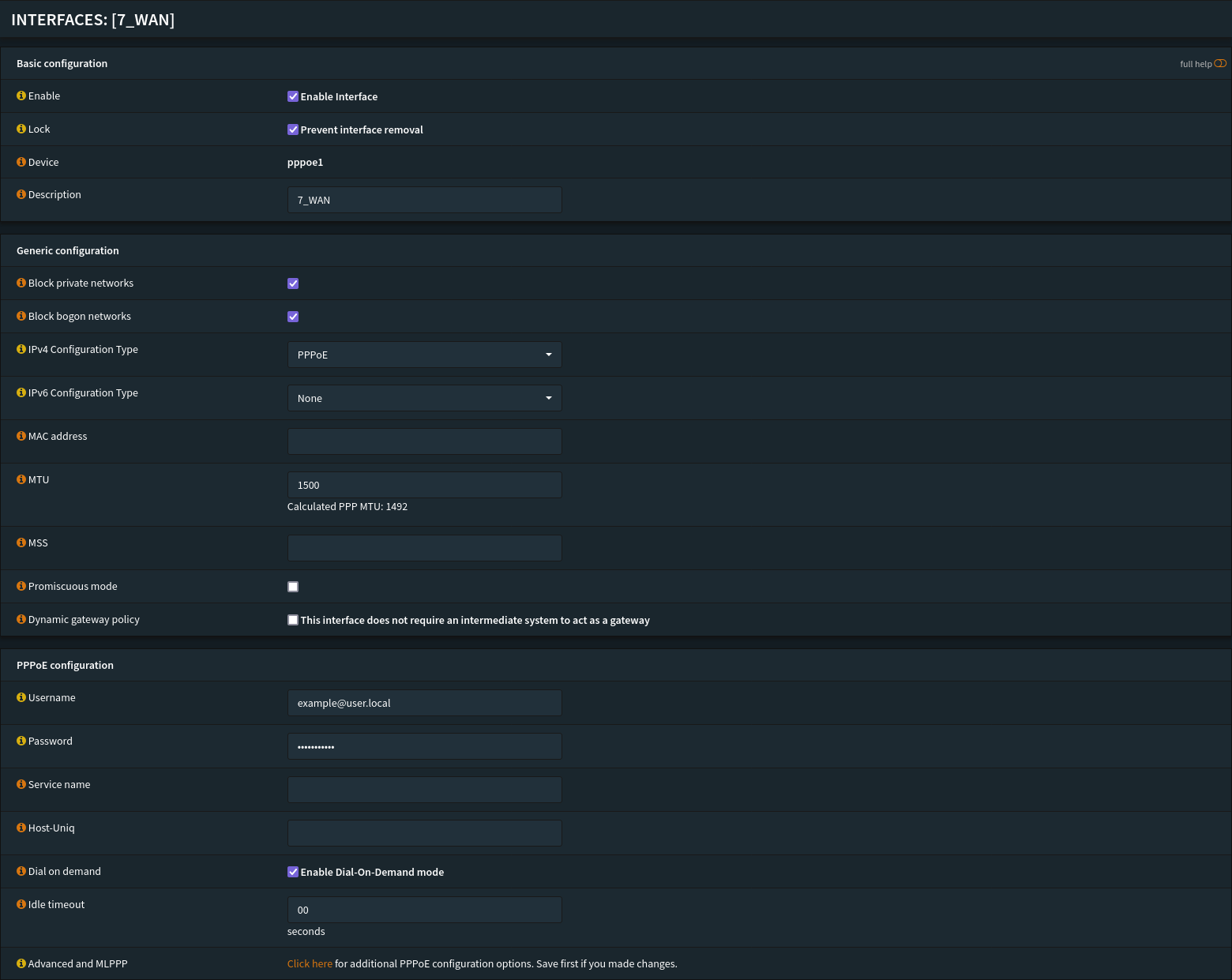
// Gateways > Configuration
- Configure the WAN interface first.
This is normally done during OPNsense installation.
- For each gateway:
- Disable Gateway Monitoring: unchecked
- Monitor IP:
9.9.9.9(Quad9) or your ISP gateway IP.- For IPv6: use
2620:fe::feor another reliable IPv6 address.
- For IPv6: use
// Settings *
Administration
- Web GUI
- Protocol:
HTTPS - SSL Certificate: needs to be created first as described in section internal CA or ACME
- HTTP Strict Transport Security: enabled
- Access Log: enabled
- Server Log: enabled
- Listen Interfaces: Restrict to admin/management subnet
- Protocol:
- Secure Shell
- Secure Shell Server: Disabled by default (enable only if needed)
- Listen Interfaces: Restrict to admin/management subnet
- Authentication
- Server: Choose TOTP service (Access)
General
- Hostname:
opnsense(or any name you prefer) - Domain:
home.local(or your own domain - internal CA or ACME) - Time zone:
Europe/Berlin - Theme:
vicuna!!! Highly recommended using dark mode, bugs love light !!!
- Prefer IPv4 over IPv6: unchecked
- DNS Servers: leave empty; we will use Unbound
- DNS Server Options: both unchecked
- Gateway Switching: unchecked
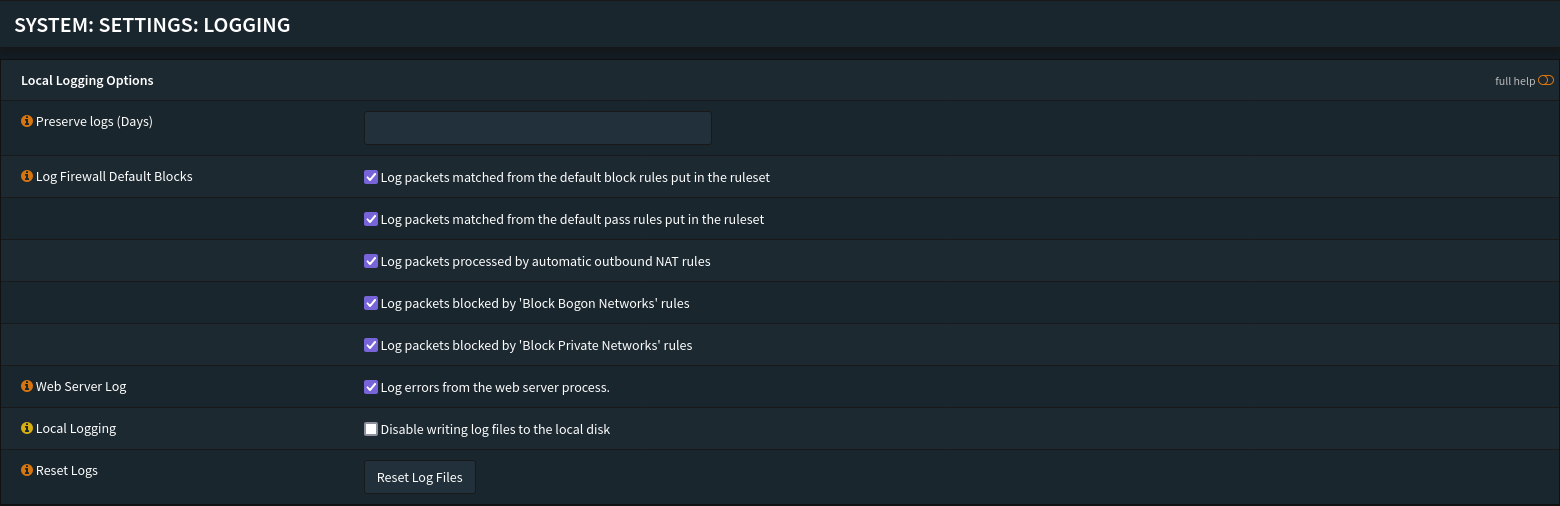
Logging
Adjust log retention and log level as needed. The defaults are usually sufficient.
Tunables
| Key | Value | Description |
|---|---|---|
hw.ibrs_disable | 1 | Disable Indirect Branch Restricted Speculation |
net.isr.maxthreads | -1 | Use at most this many CPUs for netisr processing |
net.isr.bindthreads | 1 | Bind netisr threads to CPUs |
net.isr.dispatch | deferred | netisr dispatch policy |
net.inet.rss.enabled | 1 | RSS enabled |
net.inet.rss.bits | 3 | <CORES>/4=<VALUE> RSS bits |
kern.ipc.maxsockbuf | 614400000 | 614400000=100Gbps 16777216=10Gbps Maximum socket buffer size |
net.inet.tcp.recvbuf_max | 4194304 | Max size of automatic receive buffer |
net.inet.tcp.recvspace | 65536 | Initial receive socket buffer size |
net.inet.tcp.sendspace | 65536 | Initial send socket buffer size |
net.inet.tcp.sendbuf_inc | 65536 | Incrementor step size of automatic send buffer |
net.inet.tcp.sendbuf_max | 4194304 | Max size of automatic send buffer |
net.inet.tcp.soreceive_stream | 1 | Using soreceive_stream for TCP sockets |
net.inet.tcp.mssdflt | 1240 | Default TCP Maximum Segment Size |
net.inet.tcp.abc_l_var | 52 | Cap the max cwnd increment during slow-start to this number of segments |
net.inet.tcp.minmss | 536 | Minimum TCP Maximum Segment Size |
net.isr.defaultqlimit | 2048 | Default netisr per-protocol, per-CPU queue limit if not set by protocol |
kern.random.fortuna.minpoolsize | 128 | Minimum pool size necessary to cause a reseed |
net.pf.source_nodes_hashsize | 1048576 | |
kern.hz | 1000 | Number of clock ticks per second (improve for shaper on vm’s) |
// Trust > *
Authorities
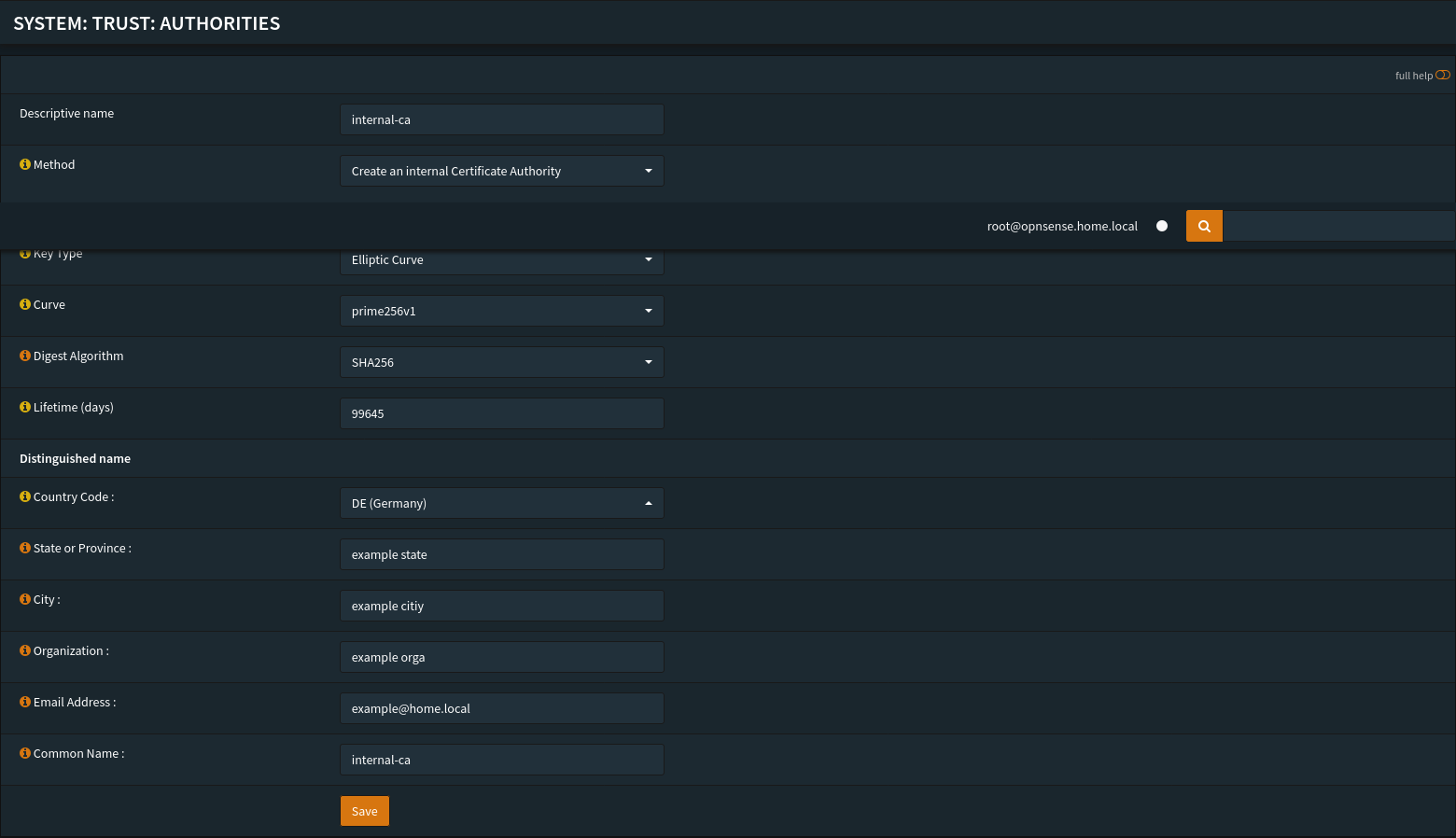
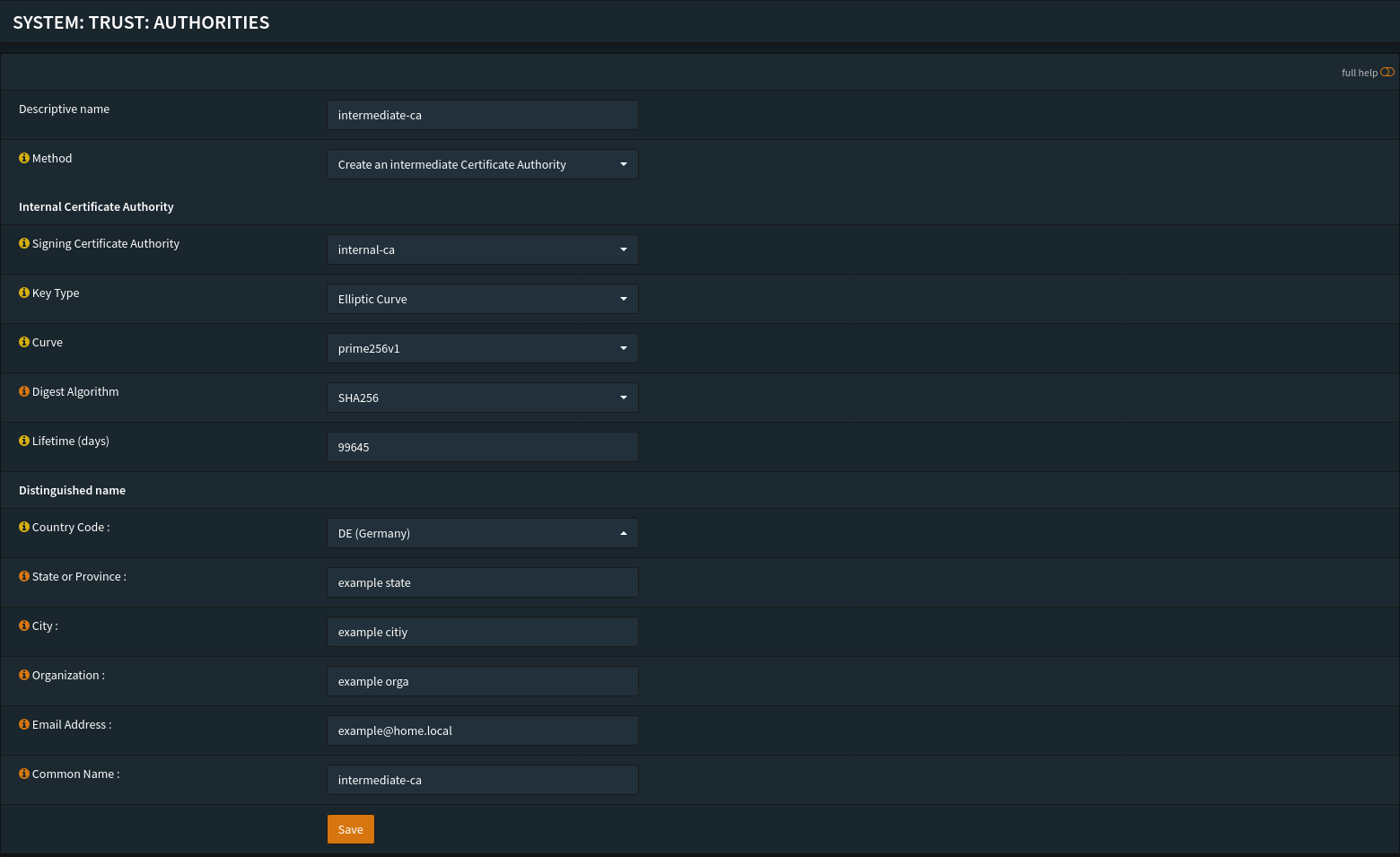
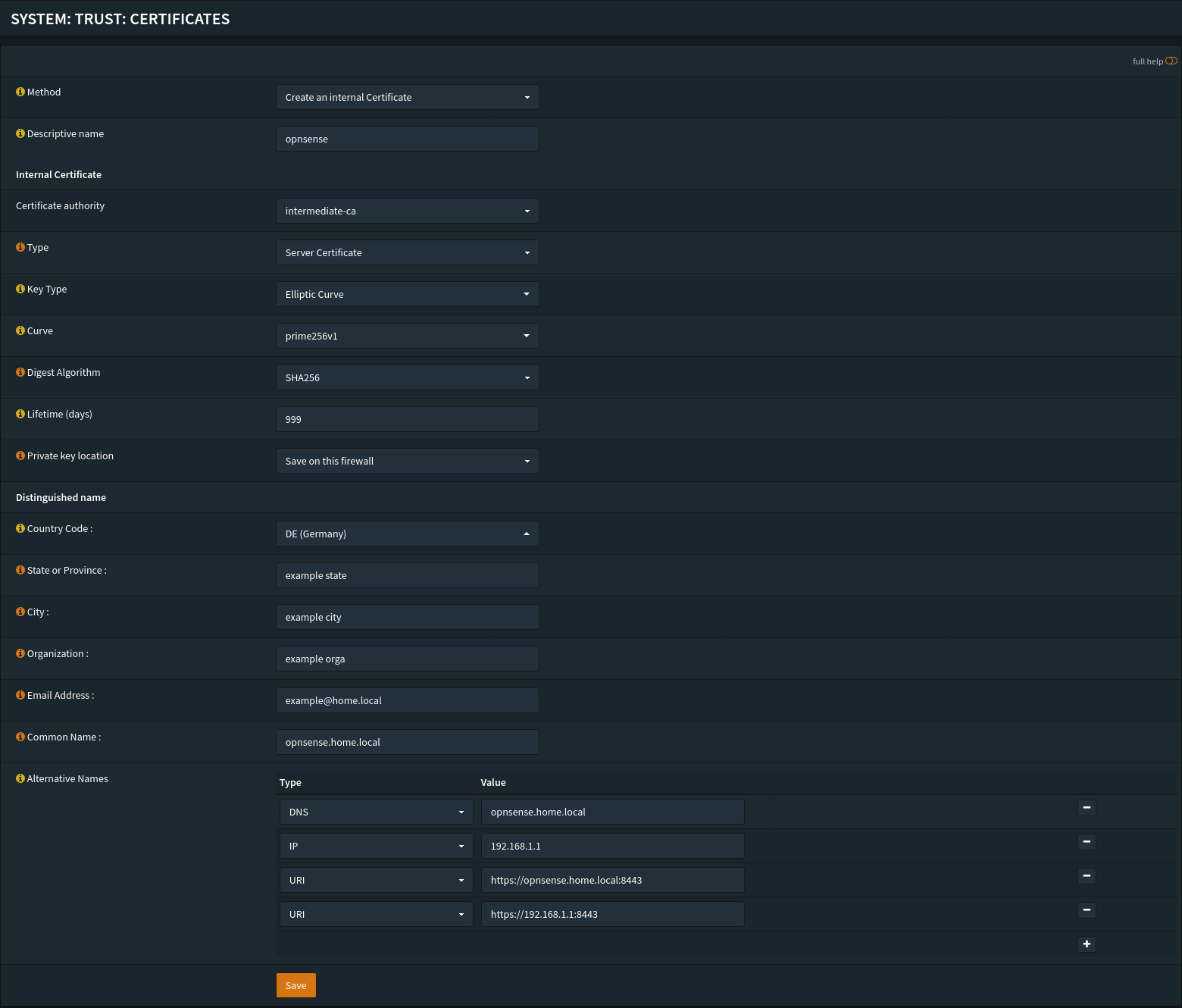
Create an internal root CA and an intermediate CA to sign internal certificates. (You can skip this part if you want to use ACME only.)
- Root CA:
internal-ca(kept offline if possible) - Intermediate CA:
intermediate-ca(used for daily certs)
Certificates
- For quick and unsigned certificate: generate an OPNsense certificate signed by your intermediate CA.
- For a signed certificate: use os-acme-client (ACME) to issue a valid, auto-renewed certificate for the OPNsense GUI (e.g.,
opnsense.example.com).
\\ Interfaces > *
- Assignments
- Settings
\\ Firewall > *
// Aliases > GeoIP settings
Add the following URL (replace <LICENSE-KEY>):
https://download.maxmind.com/app/geoip_download?edition_id=GeoLite2-Country-CSV&license_key=<LICENSE-KEY>&suffix=zip
// Aliases > Aliases
- Type: Host(s)
- IP_S_DNS_NTP_INTERN
- Content:
192.168.1.1,fd00:affe:affe:1::1Example IPs for default DNS and NTP used in this documentation and allowed internal rules.
- Statistics: checked
- Description: IP: service internal DNS+NTP (IPv4+IPv6)
- Content:
- IP_S_MDNS_SSDP
- Content:
ff02::fb,224.0.0.251,239.255.255.250 - Statistics: checked
- Description: IP: mDNS and SSDP hosts
- Content:
- IP_S_DNS_NTP_INTERN
- Type: Network(s)
- SUB_MULTI_BROAD
- Content:
ff00::/8,224.0.0.0/4,255.255.255.255,ff02::1,ff02::c,ff02::fb,ff02::1:2 - Statistics: checked
- Description: SUB: multicast + broadcast (IPv4+IPv6)
- Content:
- SUB_PRIV4
- Content:
10.0.0.0/8,172.16.0.0/12,192.168.0.0/16 - Statistics: checked
- Description: SUB: RFC1918 IPv4 private net
- Content:
- SUB_PRIV6
- Content:
fd00:affe:affe:0::0/48Example IPv6 ULA, adjust to your own range.
- Statistics: checked
- Description: SUB: RFC4193 IPv6 ULA
- Content:
- SUB_PRIV_BOGON
- Content:
10.0.0.0/8,172.16.0.0/12,192.168.0.0/16,127.0.0.0/8,224.0.0.0/4,255.255.255.255,fe80::/10,::1/128,ff00::/8,fc00::/7,ff02::1,ff02::2,2001:db8::/32,::/128,2002::/16,3ffe::/16 - Statistics: checked
- Description: SUB: RFC1918+Bogon+Local+Multicast+Additional
- Content:
- SUB_LINK_LOCAL6
- Content:
fe80::/10 - Statistics: checked
- Description: SUB: IPv6 link local
- Content:
- SUB_SITE_MC
- Content:
239.254.0.0/16 - Statistics: checked
- Description: SUB: site-local multicast (RFC2365)
- Content:
- SUB_GLOBAL6
- Content:
2000::/3 - Statistics: checked
- Description: SUB: IPv6 global unicast
- Content:
- SUB_ULA6
- Content:
fd00::/8 - Statistics: checked
- Description: SUB: IPv6 unique local address
- Content:
- SUB_MULTI_BROAD
- Type: URL Table (IPs)
- URL_BLOCKLIST
- Content:
https://ipv64.net/blocklists/ipv64_blocklist_all.txt - Statistics: checked
- Content:
- URL_BLOCKLIST
- Type: Port(s)
- PORT_DNS_BLOCK
- Content:
53,853,2853,5355,9953 - Description: PORT: DNS block ports
- Content:
- PORT_LB_NOLOG
- Content:
53,2055,9200 - Description: PORT: loopback no-log
- Content:
- PORT_S_MDNS
- Content:
5353,5540 - Description: PORT: mDNS (IoT/Thread)
- Content:
- PORT_S_SIP
- Content:
3478,3479,5060,7078:7109,10000:30000 - Description: PORT: SIP service
- Content:
- PORT_DNS_BLOCK
// Groups
Create groups as needed, e.g. default public net access groups.
- Name: G_PUB_NET4_D
- Description: default public net access [IPv4]
- Members: add interfaces which should have internet access
- Sequence:
5 - (no) GUI groups: checked
- Name: G_PUB_NET6_D
- Description: default public net access [IPv6]
- Members: add interfaces which should have internet access
- Sequence:
6 - (no) GUI groups: checked
// NAT > Port Forward
Forward NTP/DNS traffic to the firewall instead of blocking it.
- Description: PF:: forward NTP to local [IPv4]
- Interface: select interfaces
- TCP/IP Version: IPv4
- Protocol: UDP
- Source / Invert: unchecked
- Source: SUB_PRIV4
- Destination / Invert: checked
- Destination: IP_S_DNS_NTP_INTERN
- Destination port range: 123
- Redirect target IP: IP_S_DNS_NTP_INTERN
- Log: checked
- Filter rule association: None
- Description: PF:: forward NTP to local [IPv6]
- Interface: select interfaces
- TCP/IP Version: IPv6
- Protocol: UDP
- Source / Invert: unchecked
- Source: any
- Destination / Invert: checked
- Destination: IP_S_DNS_NTP_INTERN
- Destination port range: 123
- Redirect target IP: IP_S_DNS_NTP_INTERN
- Log: checked
- Filter rule association: None
- Description: PF:: forward DNS to local [IPv4]
- Interface: G_PUB_NET4_D
- TCP/IP Version: IPv4
- Protocol: TCP/UDP
- Source / Invert: unchecked
- Source: SUB_PRIV4
- Destination / Invert: checked
- Destination: IP_S_DNS_NTP_INTERN
- Destination port range: 53
- Redirect target IP: IP_S_DNS_NTP_INTERN
- Log: checked
- Filter rule association: None
- Description: PF:: forward DNS to local [IPv6]
- Interface: G_PUB_NET6_D
- TCP/IP Version: IPv6
- Protocol: TCP/UDP
- Source / Invert: unchecked
- Source: any
- Destination / Invert: checked
- Destination: IP_S_DNS_NTP_INTERN
- Destination port range: 53
- Redirect target IP: IP_S_DNS_NTP_INTERN
- Log: checked
- Filter rule association: None
// Rules
Floating
- Description: ALLOW:: F: NTP internal [IPv4+IPv6]
- Action: Pass
- Quick: checked
- Interface: none
- Direction: in
- TCP/IP Version: IPv4+IPv6
- Protocol: UDP
- Source / Invert: unchecked
- Source: SUB_PRIV4, SUB_PRIV6
- Destination / Invert: unchecked
- Destination: IP_S_DNS_NTP_INTERN
- Destination port range: 123
- Log: checked
- Description: ALLOW:: F: mDNS [IPv4+IPv6]
- Action: Pass
- Quick: checked
- Interface: none
- Direction: in
- TCP/IP Version: IPv4+IPv6
- Protocol: UDP
- Source / Invert: unchecked
- Source: SUB_PRIV4, SUB_PRIV6, SUB_LINK_LOCAL6
- Destination / Invert: unchecked
- Destination: IP_S_MDNS_SSDP
- Destination port range: 5353
- Log: checked
- Description: ALLOW:: F: MLD internal [IPv6]
- Action: Pass
- Quick: checked
- Interface: none
- Direction: in
- TCP/IP Version: IPv6
- Protocol: ICMP
- Source / Invert: unchecked
- Source: fe80::/10
- Destination / Invert: unchecked
- Destination: ff02::16/128
- Log: checked
- Description: BLOCK:: F: DNS outside [IPv4+IPv6]
- Action: Block
- Quick: checked
- Interface: none
- Direction: in
- TCP/IP Version: IPv4+IPv6
- Protocol: TCP/UDP
- Source / Invert: unchecked
- Source: any
- Destination / Invert: checked
- Destination: IP_S_DNS_NTP_INTERN
- Destination port range: PORT_DNS_BLOCK
- Log: checked
- Description: BLOCK:: F: no rule WAN [IPv4]
- Action: Block
- Quick: unchecked
- Interface: none
- Direction: in
- TCP/IP Version: IPv4
- Protocol: any
- Source / Invert: unchecked
- Source: any
- Destination / Invert: unchecked
- Destination: any
- Log: checked
- Description: BLOCK:: F: no rule local [IPv4]
- Action: Block
- Quick: unchecked
- Interface: none
- Direction: in
- TCP/IP Version: IPv4
- Protocol: any
- Source / Invert: unchecked
- Source: any
- Destination / Invert: unchecked
- Destination: SUB_PRIV_BOGON, SUB_MULTI_BROAD
- Log: checked
- Description: BLOCK:: F: no rule WAN [IPv6]
- Action: Block
- Quick: unchecked
- Interface: none
- Direction: in
- TCP/IP Version: IPv6
- Protocol: any
- Source / Invert: unchecked
- Source: any
- Destination / Invert: unchecked
- Destination: any
- Log: checked
- Description: BLOCK:: F: no rule local [IPv6]
- Action: Block
- Quick: unchecked
- Interface: none
- Direction: in
- TCP/IP Version: IPv6
- Protocol: any
- Source / Invert: unchecked
- Source: any
- Destination / Invert: unchecked
- Destination: SUB_PRIV_BOGON, SUB_MULTI_BROAD, SUB_PRIV6
- Log: checked
00_WAN
- Description: BLOCK:: WAN: blocklist (in)
- Action: Block
- Quick: checked
- Interface: 00_WAN
- Direction: in
- TCP/IP Version: IPv4+IPv6
- Protocol: any
- Source / Invert: unchecked
- Source: URL_BLOCKLIST
- Destination / Invert: unchecked
- Destination: any
- Log: checked
- Description: BLOCK:: WAN: no rule [IPv4]
- Action: Block
- Quick: checked
- Interface: 00_WAN
- Direction: in
- TCP/IP Version: IPv4
- Protocol: any
- Source / Invert: unchecked
- Source: any
- Destination / Invert: unchecked
- Destination: any
- Log: checked
- Description: BLOCK:: WAN: no rule [IPv6]
- Action: Block
- Quick: checked
- Interface: 00_WAN
- Direction: in
- TCP/IP Version: IPv6
- Protocol: any
- Source / Invert: unchecked
- Source: any
- Destination / Invert: unchecked
- Destination: any
- Log: checked
G_PUB_NET4_D
- Description: BLOCK:: GPN4D: DNS outside [IPv4+IPv6]
- Action: Block
- Quick: checked
- Interface: G_PUB_NET4_D
- Direction: in
- TCP/IP Version: IPv4+IPv6
- Protocol: TCP/UDP
- Source / Invert: unchecked
- Source: any
- Destination / Invert: checked
- Destination: IP_S_DNS_NTP_INTERN
- Destination port range: PORT_DNS_BLOCK
- Log: checked
- Description: ALLOW:: GPN4D: DNS inside [IPv4+IPv6]
- Action: Pass
- Quick: checked
- Interface: G_PUB_NET4_D
- Direction: in
- TCP/IP Version: IPv4+IPv6
- Protocol: TCP/UDP
- Source / Invert: unchecked
- Source: G_PUB_NET4_D net
- Destination / Invert: unchecked
- Destination: IP_S_DNS_NTP_INTERN
- Destination port range: 53
- Log: checked
- Description: ALLOW:: GPN4D: internet [IPv4]
- Action: Pass
- Quick: checked
- Interface: G_PUB_NET4_D
- Direction: in
- TCP/IP Version: IPv4
- Protocol: any
- Source / Invert: unchecked
- Source: G_PUB_NET4_D net
- Destination / Invert: checked
- Destination: SUB_PRIV_BOGON
- Log: checked
G_PUB_NET6_D
- Description: BLOCK:: GPN6D: DNS outside [IPv4+IPv6]
- Action: Block
- Quick: checked
- Interface: G_PUB_NET6_D
- Direction: in
- TCP/IP Version: IPv4+IPv6
- Protocol: TCP/UDP
- Source / Invert: unchecked
- Source: any
- Destination / Invert: checked
- Destination: IP_S_DNS_NTP_INTERN
- Destination port range: PORT_DNS_BLOCK
- Log: checked
- Description: ALLOW:: GPN6D: DNS inside [IPv4+IPv6]
- Action: Pass
- Quick: checked
- Interface: G_PUB_NET6_D
- Direction: in
- TCP/IP Version: IPv4+IPv6
- Protocol: TCP/UDP
- Source / Invert: unchecked
- Source: G_PUB_NET6_D net
- Destination / Invert: unchecked
- Destination: IP_S_DNS_NTP_INTERN
- Destination port range: 53
- Log: checked
- Description: ALLOW:: GPN6D: internet [IPv6]
- Action: Pass
- Quick: checked
- Interface: G_PUB_NET6_D
- Direction: in
- TCP/IP Version: IPv6
- Protocol: any
- Source / Invert: unchecked
- Source: G_PUB_NET6_D net
- Destination / Invert: checked
- Destination: SUB_PRIV_BOGON
- Log: checked
LOOPBACK
- Description: ALLOW:: LB:: 9200
- Action: Pass
- Quick: checked
- Interface: Loopback
- Direction: out
- TCP/IP Version: IPv4
- Protocol: TCP/UDP
- Source / Invert: unchecked
- Source: 127.0.0.1/32
- Destination / Invert: unchecked
- Destination: 127.0.0.1/32
- Destination port range: PORT_LB_NOLOG
- Log: unchecked
// Shaper
| direction | config | value |
|---|---|---|
| down :: Pipes | Bandwidth | XY Mbit/s |
| Queue | 2 | |
| Scheduler type | FlowQueue-CoDel | |
| (FQ-)CoDel ECN | checked | |
| FQ-CoDel quantum | 300*(<Bandwidth>/100) = X or 1514 | |
| Description | WAN-Download-Pipe | |
| down :: Queues | Pipe | WAN-Download-Pipe |
| Weight | 100 | |
| mask | destination | |
| (FQ-)CoDel ECN | checked | |
| Description | WAN-Download-Queue | |
| down :: Rules | Sequence | 2 |
| Interface | 00_WAN | |
| Protocol | ip | |
| Source | any | |
| Src-port | any | |
| Destination | any | |
| Dst-port | any | |
| Direction | in | |
| Target | WAN-Download-Queue | |
| Description | WAN-Download-Rule | |
| up :: Pipes | Bandwidth | XY Mbit/s |
| Queue | empty | |
| Scheduler type | FlowQueue-CoDel | |
| (FQ-)CoDel ECN | checked | |
| FQ-CoDel quantum | 300*(<Bandwidth>/100) = X or 1514 or empty | |
| Description | WAN-Upload-Pipe | |
| up :: Queues | Pipe | WAN-Upload-Pipe |
| Weight | 100 | |
| mask | source | |
| (FQ-)CoDel ECN | checked | |
| Description | WAN-Upload-Queue | |
| up :: Rules | Sequence | 2 |
| Interface | 00_WAN | |
| Protocol | ip | |
| Source | any | |
| Src-port | any | |
| Destination | any | |
| Dst-port | any | |
| Direction | out | |
| Target | WAN-Upload-Queue | |
| Description | WAN-Upload-Rule |
// Settings > Advanced
| Section | Key | Value |
|---|---|---|
| Bogon Networks | Update Frequency | Weekly |
| Logging | Default block | checked |
| Default pass | checked | |
| Outbound NAT | checked | |
| Bogon networks | checked | |
| Private networks | checked | |
| Miscellaneous | Firewall Optimization | conservative |
| Disable anti-lockout | checked (Only when you created relevant firewall rules, else you will lock you out) | |
| Disable sshlockout | checked (Only when you created relevant firewall rules, else you will lock you out) |
\\ Services > *
// Dnsmasq DNS & DHCP
Verify
ISC DHCPv4/6andKea DHCPare not auto-enabled before configuration.
General
| Section | Key | Value |
|---|---|---|
| Default | Enable | checked |
| Interface | Select all interfaces where you want enable DHCP | |
| DNS | Listen port | 53053 |
| DNSSEC | unchecked | |
| No hosts lookup | unchecked | |
| DNS Query Forwarding | Query DNS servers sequentially | unchecked |
| Require domain | unchecked | |
| Do not forward to system defined DNS servers | checked | |
| Do not forward private reverse lookups | unchecked | |
| DHCP | DHCP FQDN | checked |
| DHCP default domain | empty | |
| DHCP local domain | checked | |
| DHCP authoritative | unchecked | |
| DHCP reply delay | unchecked | |
| DHCP register firewall rules | checked | |
| Router advertisements | unchecked | |
| Disable HA sync | unchecked | |
| ISC / KEA DHCP (legacy) | Register ISC DHCP4 leases | unchecked |
| DHCP domain override | unchecked | |
| Register DHCP static mappings | unchecked | |
| Prefer DHCP | unchecked |
DHCP ranges
Define your required DHCP ranges for the subnets you created in Interfaces.
DHCP options
Remember we defined the DNS server under Aliases with the alias
IP_S_DNS_NTP_INTERN.
| Entry (Description) | Key | Value |
|---|---|---|
| Default DNS [IPv4] | Interface | Any |
| Type | Set | |
| Option | dns-server [6] | |
| Option6 | none | |
| Value | 192.168.1.1 | |
| Default DNS [IPv6] | Interface | Any |
| Type | Set | |
| Option | none | |
| Option6 | dns-server [23] | |
| Value | [fd00:affe:affe:1::1] |
// Unbound DNS
General
| Key | Value |
|---|---|
| Enable Unbound | checked |
| Listen Port | 53 |
| Network Interfaces | All |
| Enable DNSSEC Support | unchecked |
| Enable DNS64 Support | unchecked |
| DNS64 Prefix | none |
| Enable AAAA-only mode | unchecked |
| Register ISC DHCP4 Leases | unchecked |
| DHCP Domain Override | none |
| Register DHCP Static Mappings | checked |
| Do not register IPv6 Link-Local addresses | checked |
| Do not register system A/AAAA records | checked |
| TXT Comment Support | unchecked |
| Flush DNS Cache during reload | checked |
| Local Zone Type | transparent |
| Outgoing Network Interfaces | 00_WAN |
Query Forwarding
Example with
home.localwhen used as internal domain,
plusexample.comwhen set up with ACME.
| Entry (Description) | Key | Value |
|---|---|---|
| Dnsmasq (local) | Enabled | checked |
| Domain | home.local | |
| Server IP | 127.0.0.1 | |
| Server Port | 53053 | |
| Forward first | unchecked | |
| Dnsmasq rev. (local) | Enabled | checked |
| Domain | 168.192.in-addr.arpa | |
| Server IP | 127.0.0.1 | |
| Server Port | 53053 | |
| Forward first | unchecked | |
| Dnsmasq (pub.) | Enabled | checked |
| Domain | example.com | |
| Server IP | 127.0.0.1 | |
| Server Port | 53053 | |
| Forward first | checked |
Advanced
| Section | Key | Value |
|---|---|---|
| General Settings | Hide Identity | checked |
| Hide Version | checked | |
| Prefetch DNS Key Support | checked | |
| Harden DNSSEC Data | checked | |
| Aggressive NSEC | checked | |
| Strict QNAME Minimisation | ||
| Outgoing TCP Buffers | 32 | |
| Incoming TCP Buffers | 64 | |
| Number of queries per thread | 512 | |
| Outgoing Range | 1024 | |
| Jostle Timeout | 200 | |
| Discard Timeout | 4000 | |
| Private Domains | home.local,local,example.com | |
| Serve Expired Settings | Serve Expired Responses | checked |
| Expired Record Reply TTL value | none | |
| TTL for Expired Responses | none | |
| Reset Expired Record TTL | unchecked | |
| Client Expired Response Timeout | none | |
| Logging Settings | Extended Statistics | checked |
| Log Queries | unchecked | |
| Log Replies | unchecked | |
| Tag Queries and Replies | unchecked | |
| Log local actions | unchecked | |
| Log SERVFAIL | checked | |
| Log Level Verbosity | Level 1 | |
| Log validation level | Level 0 | |
| Cache Settings | Prefetch Support | checked |
| Unwanted Reply Threshold | none | |
| Message Cache Size | 50m | |
| RRset Cache Size | 100m | |
| Maximum TTL for RRsets and messages | 86400 | |
| Maximum Negative TTL for RRsets and messages | 300 | |
| Minimum TTL for RRsets and messages | 60 | |
| TTL for Host Cache entries | 900 | |
| Keep probing down hosts | checked | |
| Number of Hosts to cache | 2000 |
DNS over TLS
Use System Nameservers: unchecked
| Server IP | Server Port | Verify CN | Description |
|---|---|---|---|
| 9.9.9.10 | 853 | dns.quad9.net | QUAD9::Unsecured: No Malware blocking, no DNSSEC validation |
| 149.112.112.10 | 853 | dns.quad9.net | QUAD9::Unsecured: No Malware blocking, no DNSSEC validation |
| 2620:fe::10 | 853 | dns.quad9.net | QUAD9::Unsecured: No Malware blocking, no DNSSEC validation |
| 2620:fe::fe:10 | 853 | dns.quad9.net | QUAD9::Unsecured: No Malware blocking, no DNSSEC validation |
// ACME
Settings
| Key | Value |
|---|---|
| Enable Plugin | checked |
| Auto Renewal | checked |
Accounts
Let’s Encrypt:
| Key | Value |
|---|---|
| Enabled | checked |
| Name | LEv2-Stage |
| Description | Let's Encrypt - Staging (testing only) |
| E-Mail Address | add your email address |
| ACME CA | Let's Encrypt Test CA |
| Key | Value |
|---|---|
| Enabled | checked |
| Name | LEv2 |
| Description | Let's Encrypt - Production (default) |
| E-Mail Address | add your email address |
| ACME CA | Let's Encrypt [default] |
Challenge Types
IONOS:
| Key | Value |
|---|---|
| Enabled | checked |
| Name | IONOS |
| Challenge Type | DNS-01 |
| DNS Service | IONOS domain |
| DNS Sleep Time | 0 |
| Prefix | create key at https://developer.hosting.ionos.de/keys (“Präfix”) |
| Secret | create key at https://developer.hosting.ionos.de/keys (“Verschlüsselung”) |
Automation
| Key | Value |
|---|---|
| Enabled | checked |
| Name | Restart OPNsense Web UI |
| Run Command | Restart OPNsense Web UI |
Certificates
| Key | Value |
|---|---|
| Enabled | checked |
| Common Name | your domain, e.g. opnsense.example.com |
| ACME Account | LEv2-Stage (testing) / LEv2 (prod) |
| Challenge Type | IONOS |
| Auto Renewal | checked |
| Key Length | ec-256 |
| Automations | Restart OPNsense Web UI |
| DNS Alias Mode | Not using DNS alias mode |
// Dynamic DNS
Settings
Ionos Example [IPv6]:
Replace
<IONOS_TOKEN>
| Key | Value |
|---|---|
| Enabled | checked |
| Description | IONOS IPv6 |
| Service | custom |
| Protocol | Custom GET |
| Server | https://api.hosting.ionos.com/dns/v1/dyndns?q=<IONOS_TOKEN>&ipv6=__MYIP__ |
| Hostname(s) | full domain name (e.g. dyn.example.com) |
| Check ip method | Interface [IPv6] |
| Interface to monitor | 00_WAN |
| Force SSL | checked |
Ionos Example [IPv4]:
Replace
<IONOS_TOKEN>
| Key | Value |
|---|---|
| Enabled | checked |
| Description | IONOS IPv4 |
| Service | custom |
| Protocol | Custom GET |
| Server | https://api.hosting.ionos.com/dns/v1/dyndns?q=<IONOS_TOKEN> |
| Hostname(s) | full domain name (e.g. dyn.example.com) |
| Check ip method | ipify-ipv4 |
| Interface to monitor | 00_WAN |
| Force SSL | checked |
General Settings
- Enable: checked
- Interval:
300
// Intrusion Detection
Settings
| Section | Key | Value |
|---|---|---|
| General Settings | Enabled | checked |
| IPS mode | unchecked | |
| Promiscuous mode | checked | |
| Interfaces | 00_WAN | |
| Detection | Pattern matcher | Hyperscan |
| Logging | Enable syslog alerts | checked |
| Enable eve syslog output | checked | |
| Rotate log | Weekly | |
| Save logs | 4 |
IPS mode requires netmap support and may affect performance. Enable only if needed.
Download
- Select all and click Download & Update Rules
- Select all and click Enable selected
Schedule
// Monit
General Settings
Add your information and credentials.
Alert Settings
Create a new entry. Below is an example mail format to be added.
Mail format (info):
Update
monit <no-reply@DOMAIN>in from to your needs.
1
2
3
4
5
6
7
from: monit <no-reply@DOMAIN>
subject: $SERVICE $EVENT at $DATE
message: Monit $ACTION $SERVICE at $DATE on $HOST:
$DESCRIPTION
Yours sincerely,
Monit
\\ Zenarmor > *
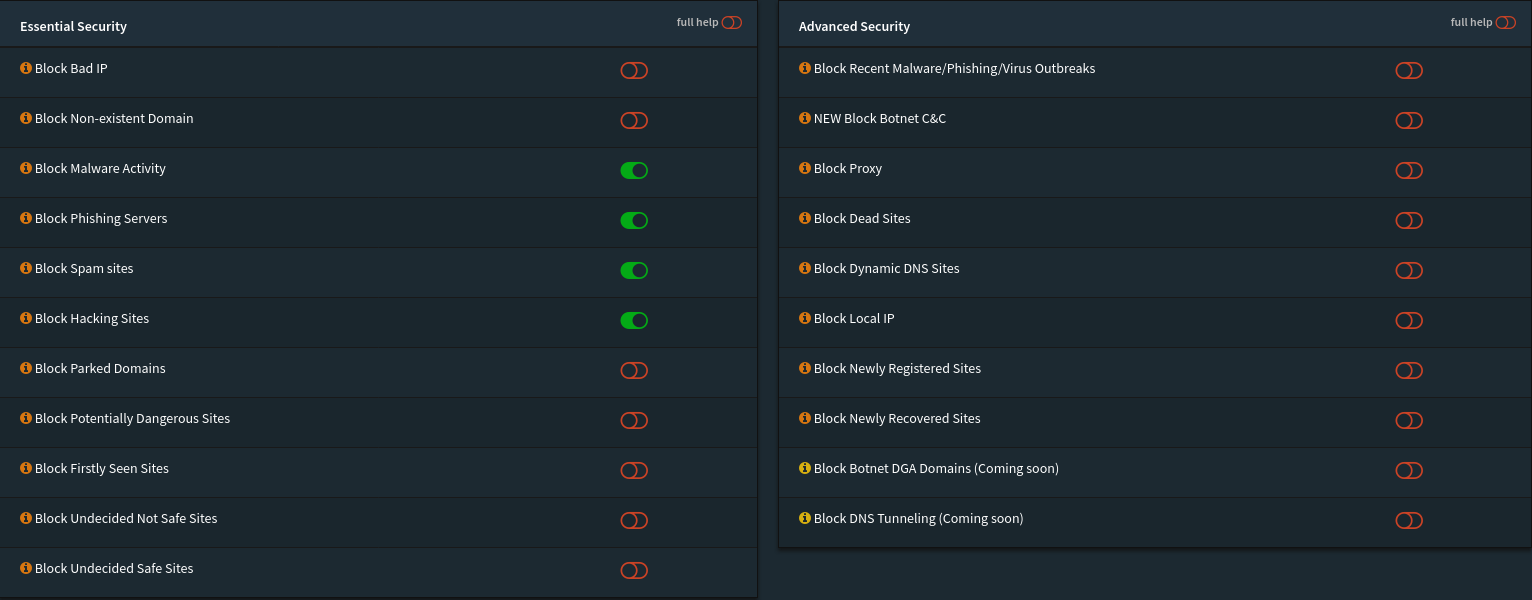
// Policies (Default)
Security
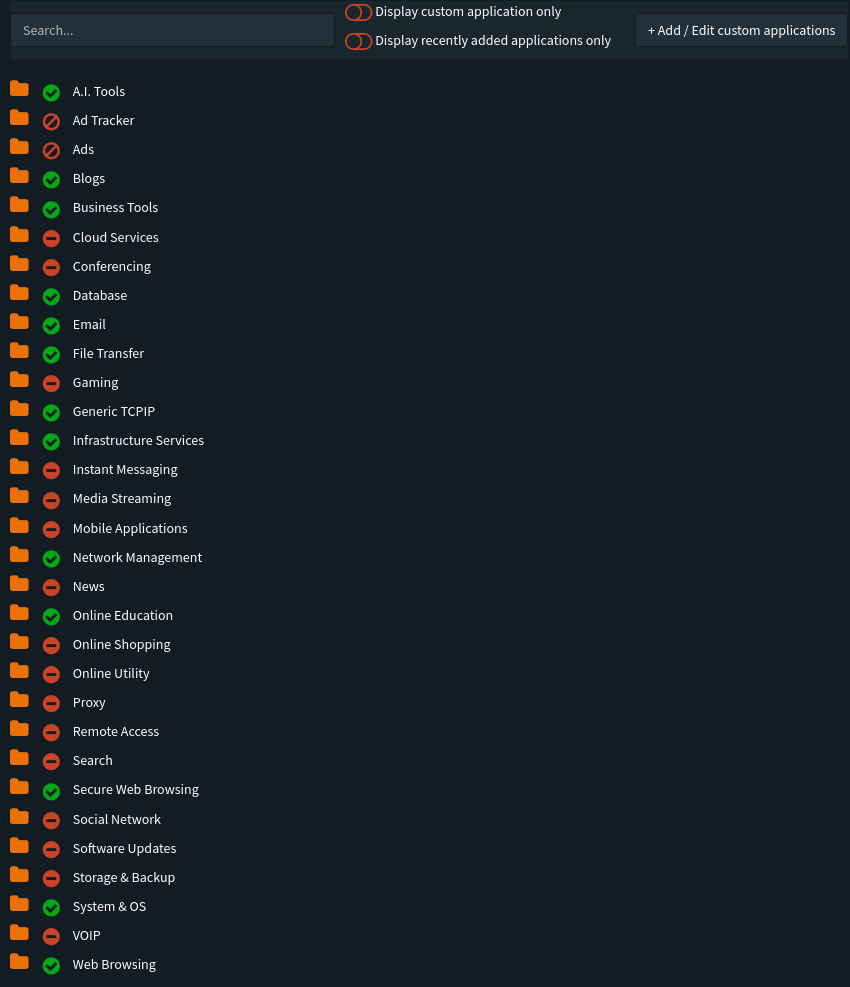
App Controls
- Cloud Services
- Apple Cloud
- Conferencing
- Google Hangouts Meet
- Gaming
- Facebook Games
- Fortnite
- Fortnite Tracker
- Microsoft Xbox
- Roblox Game
- Samsung Games
- Instant Messaging
- Facebook Chat
- Facebook Messenger
- Facebook Video call
- Google Chat
- Google Hangouts
- Media Streaming
- Apple*
- Mobile Applications
- Amazon Firestick TV
- News
- Apple News
- Bild.de
- Online Shopping
- Apple Appstore
- Apple Store
- Microsoft Wallet
- Online Utility
- Apple*
- Microsoft Cortana
- Microsoft MSDN
- Microsoft Weather
- Pivotal Tracker
- Proxy
- iCloud Private Relay
- Remote Access
- all except
- Microsoft Continuum
- Secure Shell
- Teamviewer
- all except
- Search
- Microsoft Bing
- Social Network
- Facebook*
- Google*
- facebook.comment
- facebook.statusUpdate
- Software Updates
- Apple Pipeline
- Apple Telemetry
- Intel Telemetry
- Malwarebytes Telemetry
- Microsoft Telemetry
- Mozilla Telemetry
- Windows Problem Reporting
- Storage & Backup
- all except
- Google Drive
- Microsoft OneDrive
- all except
- VOIP
- Facebook Call
Web Controls
// Configuration > *
General
- choose: Routed Mode (L3 Mode, Reporting + Blocking) with native netmap driver
- select your Interfaces Selection
- define your needs for Deployment
- set your needs for Logger
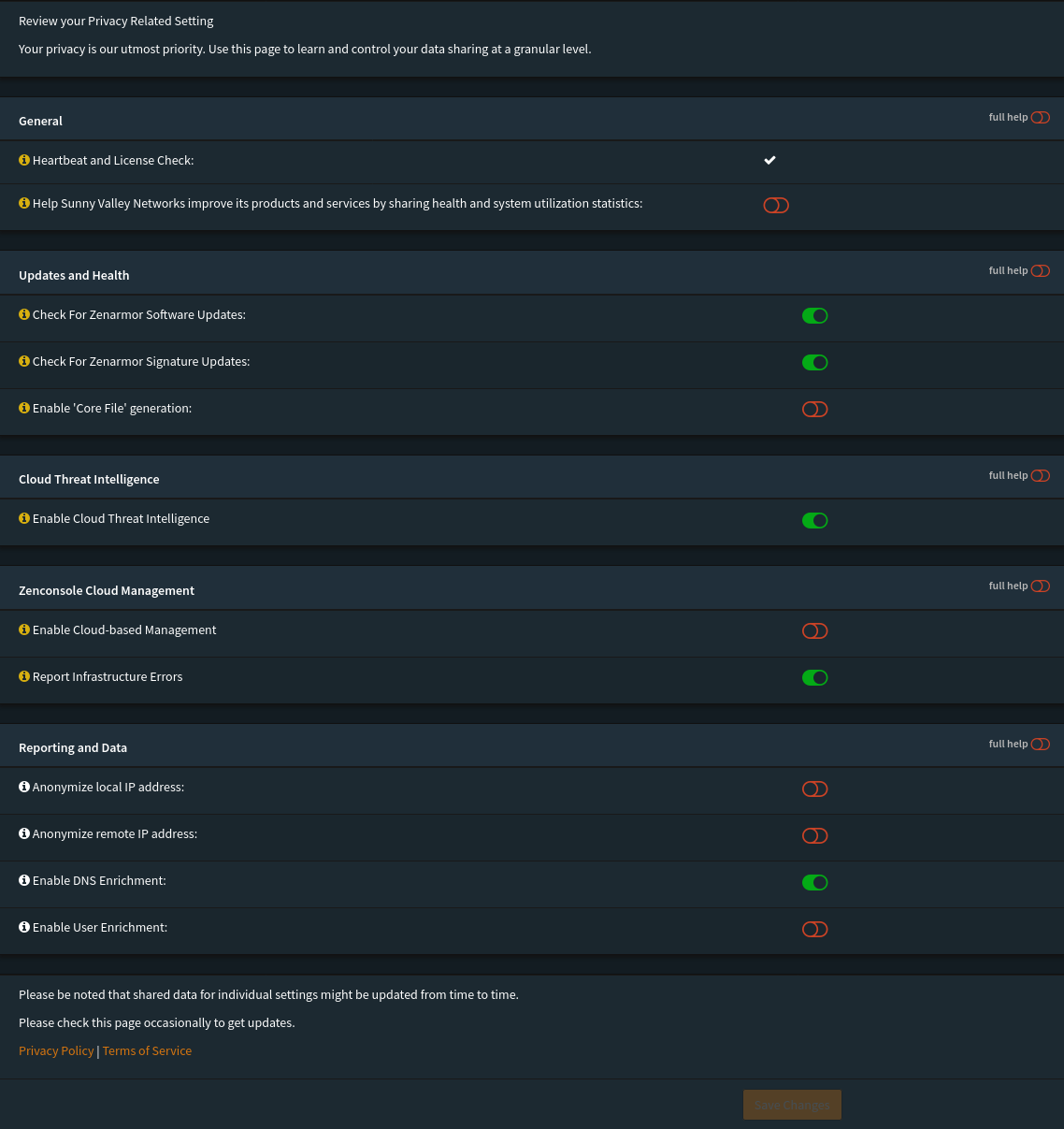
Cloud Threat Intel
- Local Domains Name To Exclude From Cloud Queries:
home.local,local
Updates & Health
- Help Sunny Valley Networks improve its products and services by sharing health and system utilization statistics: unchecked
Reporting & Data
- set your needs for Reports Data Management
- activate Scheduled Reports if needed
Privacy
\\ Resources & More information
- https://docs.opnsense.org/
- https://en.wikipedia.org/wiki/Private_network
- https://ipgeolocation.io/resources/bogon.html
- https://forum.opnsense.org/index.php?PHPSESSID=ahi5e19a2tl303rir594sgmn88&topic=27394.msg160740#msg160740
- tunings
- https://docs.opnsense.org/troubleshooting/performance.html
- https://teklager.se/en/knowledge-base/opnsense-performance-optimization
- https://binaryimpulse.com/2022/11/opnsense-performance-tuning-for-multi-gigabit-internet
- https://www.reddit.com/r/OPNsenseFirewall/comments/b2uhpw/performance_tuning_help
- https://calomel.org/freebsd_network_tuning.html
- https://docs.opnsense.org/troubleshooting/performance.html
- https://www.reddit.com/r/opnsense/comments/14li2c7/10gbps_speed/
- https://www.reddit.com/r/opnsense/comments/17fjbbw/opnsense_on_proxmox_10gb_network_woes/
- https://forum.opnsense.org/index.php?topic=31830.0
- https://forum.opnsense.org/index.php?topic=18754.150
- https://medium.com/@truvis.thornton/opnsense-firewall-configuration-performance-tuning-for-multi-gigabit-internet-and-better-speeds-in-cfc80c49c544
- https://docs.opnsense.org/manual/shaping.html